-
EndBlock EDR
-
More

資料處理中, 請稍候...
Loading...
Get your price estimate immediately after completing the steps online.
|
|
Item | Unit Price | Quantity | Subtotal (excl. tax) | Total (incl. tax) | Remove |
|---|
 Once your order is complete, we'll send the order details to your email.
Once your order is complete, we'll send the order details to your email.
Please note: Discounts such as member points and coupon codes are calculated based on the pricing on the date of the price estimation. Be sure to check the validity period before use.
 Cart Details
Cart Details
Below is a summary of your estimated order.
To view the full quotation, please click "Download complete quote".



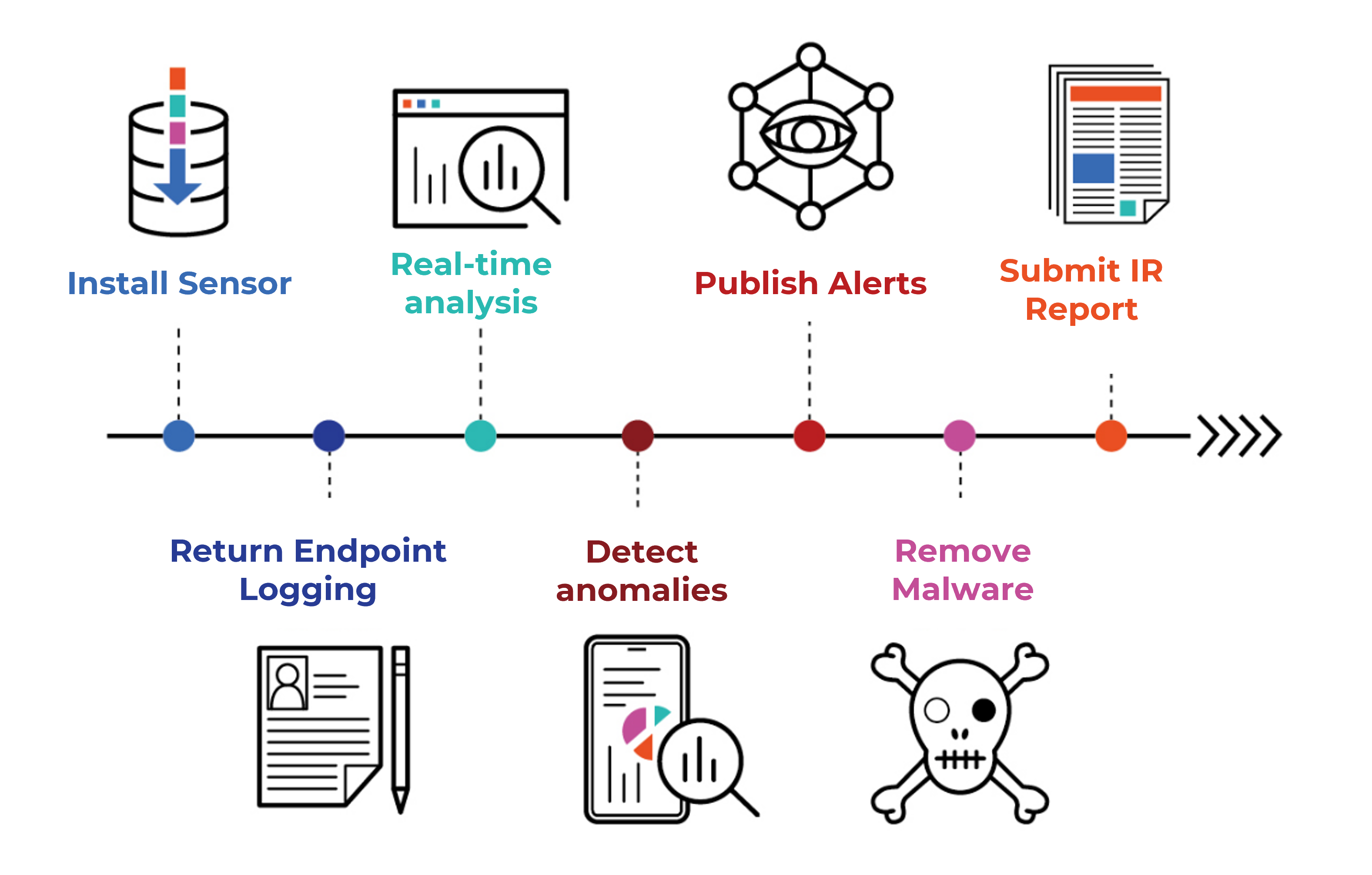
EndBlock captures all endpoint behavior, providing a full view of cyberattacks by tracing all compromised footprints and analyzing the hacker’s intrusion methods.

 Service Hotline
Service Hotline
Customer service hours 9:00 - 18:00
 Contact Email
Contact Email
Send your valuable comments by E-mail
We'll reply within 3–5 days after receiving your message.

 Request for Quotation
Request for Quotation